Cryptography is the practice and study of techniques for securing communication and information. Its primary purpose is to ensure confidentiality, integrity, and authenticity in the digital world. As the backbone of modern security protocols, cryptography plays a crucial role in protecting sensitive data from unauthorized access and ensuring secure transactions in various applications, including online banking, e-commerce, and private communications.
Cryptography: Symmetric and Asymmetric Techniques || क्रिप्टोग्राफी: सममित और असममित तकनीकों
Historical Context
The roots of cryptography can be traced back to ancient civilizations. Early forms of it included simple substitution ciphers, where letters in a message were replaced with other letters. Notable historical examples include:
- Caesar Cipher: Named after Julius Caesar, this technique involved shifting the letters of the alphabet by a fixed number.
- Vigenère Cipher: A more complex method that used a keyword to determine the letter shifts, making it more resistant to frequency analysis.
With the advent of the digital age, cryptography evolved significantly, leading to the development of modern encryption algorithms that are far more complex and secure.
Types of Cryptography
It can be categorized into several types, each serving different purposes:
- Symmetric Cryptography:
- Involves a single key for both encryption and decryption.
- Fast and efficient for large amounts of data.
- Examples: AES (Advanced Encryption Standard), DES (Data Encryption Standard).
- Asymmetric Cryptography:
- Utilizes a pair of keys: a public key for encryption and a private key for decryption.
- Provides secure key exchange and digital signatures.
- Examples: RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography).
- Hash Functions:
- Converts data into a fixed-size string of characters, which is typically a hash value.
- Primarily used for data integrity and verification.
- Examples: SHA-256 (Secure Hash Algorithm), MD5 (Message Digest Algorithm 5).
Symmetric Cryptography
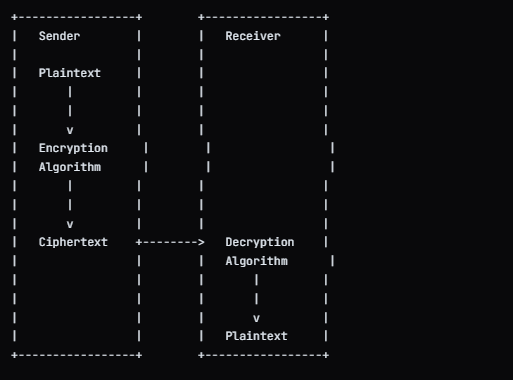
Definition: It, also known as secret-key cryptography, uses a single key for both encryption and decryption. This means that both the sender and the receiver must possess the same key to communicate securely.
How It Works:
- Key Generation: A secret key is generated, which is shared between the communicating parties.
- Encryption: The plaintext message is transformed into ciphertext using the shared key and a symmetric encryption algorithm.
- Transmission: The ciphertext is sent over the communication channel.
- Decryption: The recipient uses the same key to convert the ciphertext back to plaintext.
Example Algorithms:
- AES (Advanced Encryption Standard): Widely used in various applications, AES supports key sizes of 128, 192, and 256 bits and is known for its speed and security.
- DES (Data Encryption Standard): An older standard that uses a 56-bit key, now considered insecure due to vulnerabilities.
Advantages:
- Speed: Symmetric algorithms are generally faster than asymmetric ones, making them suitable for encrypting large amounts of data.
- Efficiency: Requires less computational power, which is beneficial for devices with limited resources.
Disadvantages:
- Key Distribution: The challenge lies in securely sharing the secret key. If the key is intercepted, the security is compromised.
- Scalability: In a network with many users, the number of keys required increases significantly, complicating key management.
Asymmetric Cryptography
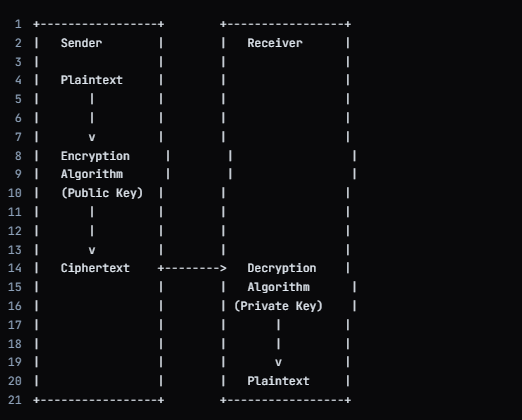
Definition: It, also known as public-key cryptography, uses a pair of keys: a public key for encryption and a private key for decryption. The public key can be shared openly, while the private key is kept secret.
How It Works:
- Key Pair Generation: Each user generates a public and private key pair.
- Encryption: The sender encrypts the plaintext using the recipient’s public key, creating ciphertext.
- Transmission: The ciphertext is sent to the recipient.
- Decryption: The recipient uses their private key to decrypt the ciphertext back to plaintext.
Example Algorithms:
- RSA (Rivest-Shamir-Adleman): A widely used asymmetric algorithm that relies on the mathematical difficulty of factoring large prime numbers.
- ECC (Elliptic Curve Cryptography): Offers similar security to RSA but with smaller key sizes, making it more efficient.
Advantages:
- Secure Key Exchange: Asymmetric allows secure communication without needing to share a secret key beforehand.
- Digital Signatures: It enables the creation of digital signatures, providing authentication and integrity verification.
Disadvantages:
- Speed: Asymmetric algorithms are generally slower than symmetric ones, making them less suitable for encrypting large data volumes.
- Complexity: More computationally intensive, which can be a drawback for resource-constrained devices.
Key Concepts in Cryptography
- Encryption: The process of converting plaintext into ciphertext to prevent unauthorized access.
- Decryption: The reverse process of converting ciphertext back to plaintext.
- Key Management: The process of handling cryptographic keys, including their generation, distribution, and storage.
- Digital Signatures: A mathematical scheme for verifying the authenticity and integrity of a message.
Applications of Cryptography
Cryptography is integral to various applications across multiple sectors:
- Secure Communications: Ensuring that messages sent over the internet remain confidential and are not tampered with.
- E-commerce: Protecting sensitive information such as credit card numbers and personal data during online transactions.
- Data Storage: Encrypting files and databases to protect against unauthorized access and breaches.
- Blockchain Technology: Securing transactions and maintaining the integrity of decentralized ledgers.
Challenges in Cryptography
Despite its importance, cryptography faces several challenges:
- Quantum Computing: The rise of quantum computers poses a threat to traditional cryptographic algorithms. Quantum algorithms could potentially break widely used encryption methods, necessitating the development of quantum-resistant algorithms.
- Key Management: Properly managing cryptographic keys is critical. Poor key management can lead to vulnerabilities and data breaches.
- User Awareness: Many users lack understanding of cryptographic principles, leading to poor security practices. Educating users about the importance of strong passwords and secure communications is essential.
Future of Cryptography
The future of cryptography will likely involve:
- Post-Quantum Cryptography: Developing new algorithms that can withstand quantum attacks.
- Homomorphic Encryption: Allowing computations on encrypted data without needing to decrypt it, enhancing privacy and security.
- Blockchain and Decentralized Identity: Leveraging cryptographic techniques to create secure, decentralized identities and enhance trust in digital transactions.
Conclusion
Cryptography is a vital component of modern security, enabling secure communication and protecting sensitive data in an increasingly digital world. As technology evolves, so too will the techniques and challenges associated with cryptography. Understanding its principles and applications is essential for individuals and organizations alike to navigate the complexities of digital security effectively.
Join us on Facebook, WhatsApp , Telegram , LinkedIn and Cert-In for latest cyber security news.



